- Feb 17, 2025
-
-
Pablo Andrés Dorado Suárez authored
Closes #4315 --------- Co-authored-by:Guillaume Thiolliere <guillaume.thiolliere@parity.io>
-
- Feb 10, 2025
-
-
Dhiraj Sah authored
# Description Fixes #7039 The Preservation of transfer method of fungible and fungibles adapters is changed from Preserve to Expendable. So the behavior of the TransferAsset will be consistent with the WithdrawAsset function, as in [fungible](https://github.com/paritytech/polkadot-sdk/blob/f3ab3854 /polkadot/xcm/xcm-builder/src/fungible_adapter.rs#L217) and [fungibles](https://github.com/paritytech/polkadot-sdk/issues/url) adapter. This pull request includes changes to the `fungible_adapter.rs` and `fungibles_adapter.rs` files in the `polkadot/xcm/xcm-builder` directory. The main change involves modifying the transfer method to use the `Expendable` strategy instead of the `Preserve` strategy. Changes to transfer strategy: * [`polkadot/xcm/xcm-builder/src/fungible_adapter.rs`](diffhunk://#diff-6ebd77385441f2c8b023c480e818a01c4b43ae892c73ca30144cd64ee960bd66L67-R67): Changed the transfer method to use `Expendable` instead of `Preserve`. * [`polkadot/xcm/xcm-builder/src/fungibles_adapter.rs`](diffhunk://#diff-82221429de4c4c88be3d2976ece6475ef4fa56a32abc70290911bd47191f8e17L61-R61): Changed the transfer method to use `Expendable` instead of `Preserve`. --------- Co-authored-by:
Francisco Aguirre <franciscoaguirreperez@gmail.com> Co-authored-by:
Adrian Catangiu <adrian@parity.io>
-
- Feb 07, 2025
-
-
Przemek Rzad authored
- Closes https://github.com/paritytech/license-scanner/issues/44 - Silent because only comments are changed in the crates. ## What's inside First, we change the file traversal mechanism from shell globbing to walking through files which happens inside the `license-scanner` - so it has knowledge about directory structure and can correlate files with corresponding Cargo manifest. Next, added `MIT-0` and `Unlicense` to the allowed list of licenses. `Unlicense` appears only once across {Substrate,Cumulus,Polkadot} - in `penpal-runtime`. Finally, updated headers in files that do not match the corresponding manifest license. --------- Co-authored-by: cornholio <0@mcornholio.ru>
cornholio <0@mcornholio.ru>
-
- Jan 30, 2025
-
-
Jeeyong Um authored
# Description Close #7122. This PR replaces the unmaintained `derivative` dependency with `derive-where`. ## Integration This PR doesn't change the public interfaces. ## Review Notes The `derivative` crate, previously used to derive basic traits for structs with generics or enums, is no longer actively maintained. It has been replaced with the `derive-where` crate, which offers a more straightforward syntax while providing the same features as `derivative`. --------- Co-authored-by:Guillaume Thiolliere <gui.thiolliere@gmail.com>
-
- Jan 27, 2025
-
-
Ron authored
Resolves (partially): https://github.com/paritytech/polkadot-sdk/issues/7148 (see _Problem 1 - `ShouldExecute` tuple implementation and `Deny` filter tuple_) This PR changes the behavior of `DenyThenTry` from the pattern `DenyIfAllMatch` to `DenyIfAnyMatch` for the tuple. I would expect the latter is the right behavior so make the fix in place, but we can also add a dedicated Impl with the legacy one untouched. ## TODO - [x] add unit-test for `DenyReserveTransferToRelayChain` - [x] add test and investigate/check `DenyThenTry` as discussed [here](https://github.com/paritytech/polkadot-sdk/pull/6838#discussion_r1914553990) and update documentation if needed --------- Co-authored-by:
Branislav Kontur <bkontur@gmail.com> Co-authored-by:
Francisco Aguirre <franciscoaguirreperez@gmail.com> Co-authored-by: command-bot <> Co-authored-by:
Clara van Staden <claravanstaden64@gmail.com> Co-authored-by:
Adrian Catangiu <adrian@parity.io>
-
- Jan 26, 2025
-
-
Branislav Kontur authored
Part of: https://github.com/paritytech/polkadot-sdk/issues/6906
-
- Jan 23, 2025
-
-
Branislav Kontur authored
This PR contains small fixes identified during work on the larger PR: https://github.com/paritytech/polkadot-sdk/issues/6906. --------- Co-authored-by: command-bot <>
-
runcomet authored
# Derived Dev Accounts Resolves https://github.com/paritytech/polkadot-sdk/issues/6040 ## Description This update introduces support for creating an arbitrary number of developer accounts at the genesis block based on a specified derivation path. This functionality is gated by the runtime-benchmarks feature, ensuring it is only enabled during benchmarking scenarios. ### Key Features - Arbitrary Dev Accounts at Genesis: Developers can now specify any number of accounts to be generated at genesis using a hard derivation path. - Default Derivation Path: If no derivation path is provided (i.e., when `Option<dev_accounts: (..., None)>` is set to `Some` at genesis), the system will default to the path `//Sender//{}`. - No Impact on Total Token Issuance: Developer accounts are excluded from the total issuance of the token supply at genesis, ensuring they do not affect the overall balance or token distribution. polkadot address: 14SRqZTC1d8rfxL8W1tBTnfUBPU23ACFVPzp61FyGf4ftUFg --------- Co-authored-by:Sebastian Kunert <skunert49@gmail.com>
-
- Jan 17, 2025
-
-
thiolliere authored
We already use it for lots of pallet. Keeping it feature gated by experimental means we lose the information of which pallet was using experimental before the migration to frame crate usage. We can consider `polkadot-sdk-frame` crate unstable but let's not use the feature `experimental`. --------- Co-authored-by: command-bot <>
-
- Jan 13, 2025
-
-
Branislav Kontur authored
## Description This PR deprecates `UnpaidLocalExporter` in favor of the new `LocalExporter`. First, the name is misleading, as it can be used in both paid and unpaid scenarios. Second, it contains a hard-coded channel 0, whereas `LocalExporter` uses the same algorithm as `xcm-exporter`. ## Future Improvements Remove the `channel` argument and slightly modify the `ExportXcm::validate` signature as part of [this issue](https://github.com/orgs/paritytech/projects/145/views/8?pane=issue&itemId=84899273). --------- Co-authored-by: command-bot <>
-
- Jan 05, 2025
-
-
thiolliere authored
Implement cumulus StorageWeightReclaim as wrapping transaction extension + frame system ReclaimWeight (#6140) (rebasing of https://github.com/paritytech/polkadot-sdk/pull/5234) ## Issues: * Transaction extensions have weights and refund weight. So the reclaiming of unused weight must happen last in the transaction extension pipeline. Currently it is inside `CheckWeight`. * cumulus storage weight reclaim transaction extension misses the proof size of logic happening prior to itself. ## Done: * a new storage `ExtrinsicWeightReclaimed` in frame-system. Any logic which attempts to do some reclaim must use this storage to avoid double reclaim. * a new function `reclaim_weight` in frame-system pallet: info and post info in arguments, read the already reclaimed weight, calculate the new unused weight from info and post info. do the more accurate reclaim if higher. * `CheckWeight` is unchanged and still reclaim the weight in post dispatch * `ReclaimWeight` is a new transaction extension in frame system. For s...
-
- Dec 20, 2024
-
-
Xavier Lau authored
It doesn't make sense to only reorder the features array. For example: This makes it hard for me to compare the dependencies and features, especially some crates have a really really long dependencies list. ```toml [dependencies] c = "*" a = "*" b = "*" [features] std = [ "a", "b", "c", ] ``` This makes my life easier. ```toml [dependencies] a = "*" b = "*" c = "*" [features] std = [ "a", "b", "c", ] ``` --------- Co-authored-by:Bastian Köcher <git@kchr.de> Co-authored-by: command-bot <>
-
- Dec 18, 2024
-
-
clangenb authored
Migrates pallet-xcm benchmarks to benchmark v2 syntax * Part of #6202
-
- Dec 12, 2024
-
-
Bastian Köcher authored
Co-authored-by:
GitHub Action <action@github.com> Co-authored-by:
Branislav Kontur <bkontur@gmail.com> Co-authored-by: command-bot <>
-
- Dec 11, 2024
-
-
Francisco Aguirre authored
`InitiateTransfer`, the new instruction introduced in XCMv5, allows preserving the origin after a cross-chain transfer via the usage of the `AliasOrigin` instruction. The receiving chain needs to be configured to allow such this instruction to have its intended effect and not just throw an error. In this PR, I add the alias rules specified in the [RFC for origin preservation](https://github.com/polkadot-fellows/RFCs/blob/main/text/0122-alias-origin-on-asset-transfers.md) to westend chains so we can test these scenarios in the testnet. The new scenarios include: - Sending a cross-chain transfer from one system chain to another and doing a Transact on the same message (1 hop) - Sending a reserve asset transfer from one chain to another going through asset hub and doing Transact on the same message (2 hops) The updated chains are: - Relay: added `AliasChildLocation` - Collectives: added `AliasChildLocation` and `AliasOriginRootUsingFilter<AssetHubLocation, Everything>` - People: added `AliasChildLocation` and `AliasOriginRootUsingFilter<AssetHubLocation, Everything>` - Coretime: added `AliasChildLocation` and `AliasOriginRootUsingFilter<AssetHubLocation, Everything>` AssetHub already has `AliasChildLocation` and doesn't need the other config item. BridgeHub is not intended to be used by end users so I didn't add any config item. Only added `AliasChildOrigin` to the relay since we intend for it to be used less. --------- Co-authored-by:GitHub Action <action@github.com> Co-authored-by: command-bot <>
-
- Dec 10, 2024
-
-
Ron authored
## Description Our smoke tests transfer `WETH` from Sepolia to Westend-AssetHub breaks, try to reregister `WETH` on AH but fails as following: https://bridgehub-westend.subscan.io/xcm_message/westend-4796d6b3600aca32ef63b9953acf6a456cfd2fbe https://assethub-westend.subscan.io/extrinsic/9731267-0?event=9731267-2 The reason is that the transact call encoded on BH to register the asset https://github.com/paritytech/polkadot-sdk/blob/a77940ba/bridges/snowbridge/primitives/router/src/inbound/mod.rs#L282-L289 ``` 0x3500020209079edaa8020300fff9976782d46cc05630d1f6ebab18b2324d6b1400ce796ae65569a670d0c1cc1ac12515a3ce21b5fbf729d63d7b289baad070139d01000000000000000000000000000000 ``` the `asset_id` which is the xcm location can't be decoded on AH in V5 Issue initial post in https://matrix.to/#/!qUtSTcfMJzBdPmpFKa:parity.io/$RNMAxIIOKGtBAqkgwiFuQf4eNaYpmOK-Pfw4d6vv1aU?via=parity.io&via=matrix.org&via=web3.foundation --------- Co-au...
-
Branislav Kontur authored
Co-authored-by:Francisco Aguirre <franciscoaguirreperez@gmail.com>
-
- Dec 09, 2024
-
-
Adrian Catangiu authored
# Description Sending XCM messages to other chains requires paying a "transport fee". This can be paid either: - from `origin` local account if `jit_withdraw = true`, - taken from Holding register otherwise. This currently works for following hops/scenarios: 1. On destination no transport fee needed (only sending costs, not receiving), 2. Local/originating chain: just set JIT=true and fee will be paid from signed account, 3. Intermediary hops - only if intermediary is acting as reserve between two untrusted chains (aka only for `DepositReserveAsset` instruction) - this was fixed in https://github.com/paritytech/polkadot-sdk/pull/3142 But now we're seeing more complex asset transfers that are mixing reserve transfers with teleports depending on the involved chains. # Example E.g. transferring DOT between Relay and parachain, but through AH (using AH instead of the Relay chain as parachain's DOT reserve). In the `Parachain --1--> AssetHub --2--> Relay` scenario, DOT has to be reserve-withdrawn in leg `1`, then teleported in leg `2`. On the intermediary hop (AssetHub), `InitiateTeleport` fails to send onward message because of missing transport fees. We also can't rely on `jit_withdraw` because the original origin is lost on the way, and even if it weren't we can't rely on the user having funded accounts on each hop along the way. # Solution/Changes - Charge the transport fee in the executor from the transferred assets (if available), - Only charge from transferred assets if JIT_WITHDRAW was not set, - Only charge from transferred assets if unless using XCMv5 `PayFees` where we do not have this problem. # Testing Added regression tests in emulated transfers. Fixes https://github.com/paritytech/polkadot-sdk/issues/4832 Fixes https://github.com/paritytech/polkadot-sdk/issues/6637 --------- Signed-off-by:
Adrian Catangiu <adrian@parity.io> Co-authored-by:
Francisco Aguirre <franciscoaguirreperez@gmail.com>
-
- Dec 08, 2024
-
-
Francisco Aguirre authored
Last feature we wanted for V5, changing `SetAssetClaimer` to be just one of many possible "hints" that you can specify at the beginning of your program to change its behaviour. This makes it easier to add new hints in the future and have barriers accept them. --------- Co-authored-by:GitHub Action <action@github.com>
-
- Dec 05, 2024
-
-
Francisco Aguirre authored
Closes: https://github.com/paritytech/polkadot-sdk/issues/6585 Removing the `require_weight_at_most` parameter in V5 Transact had only one problem. Converting a message from V5 to V4 to send to chains that didn't upgrade yet. The conversion would not know what weight to give to the Transact, since V4 and below require it. To fix this, I added back the weight in the form of an `Option<Weight>` called `fallback_max_weight`. This can be set to `None` if you don't intend to deal with a chain that hasn't upgraded yet. If you set it to `Some(_)`, the behaviour is the same. The plan is to totally remove this in V6 since there will be a good conversion path from V6 to V5. --------- Co-authored-by:
GitHub Action <action@github.com> Co-authored-by:
Adrian Catangiu <adrian@parity.io>
-
- Dec 03, 2024
-
-
Lulu authored
-
- Nov 28, 2024
-
-
Ludovic_Domingues authored
# Description Migrated pallet-xcm-benchmarks to benchmaking syntax V2 This is part of #6202 --------- Co-authored-by:Giuseppe Re <giuseppe.re@parity.io>
-
- Nov 26, 2024
-
-
Francisco Aguirre authored
The `query_weight_to_asset_fee` function was trying to convert versions by using `try_as`, this function [doesn't convert from a versioned to a concrete type](https://github.com/paritytech/polkadot-sdk/blob/0156ca8f/polkadot/xcm/src/lib.rs#L131). This would cause all calls with a lower version to fail. The correct function to use is the good old [try_into](https://github.com/paritytech/polkadot-sdk/blob/0156ca8f /polkadot/xcm/src/lib.rs#L184). Now those calls work :) --------- Co-authored-by: command-bot <> Co-authored-by:
Branislav Kontur <bkontur@gmail.com> Co-authored-by:
GitHub Action <action@github.com>
-
Branislav Kontur authored
This PR addresses two small fixes: 1. Fixed a typo ("as as") found on the way. 2. Resolved a bug in the `local/remote exporters` used for bridging. Previously, they consumed `dest` and `msg` without returning them when inner routers/exporters failed with `NotApplicable`. This PR ensures compliance with the [`SendXcm`](https://github.com/paritytech/polkadot-sdk/blob/master/polkadot/xcm/src/v5/traits.rs#L449-L450) and [`ExportXcm`](https://github.com/paritytech/polkadot-sdk/blob/master/polkadot/xcm/xcm-executor/src/traits/export.rs#L44-L45) traits. --------- Co-authored-by:GitHub Action <action@github.com>
-
- Nov 25, 2024
-
-
Branislav Kontur authored
-
- Nov 12, 2024
-
-
Francisco Aguirre authored
Added `ExecuteWithOrigin` instruction according to the old XCM RFC 38: https://github.com/polkadot-fellows/xcm-format/pull/38. This instruction allows you to descend or clear while going back again. ## TODO - [x] Implementation - [x] Unit tests - [x] Integration tests - [x] Benchmarks - [x] PRDoc ## Future work Modify `WithComputedOrigin` barrier to allow, for example, fees to be paid with a descendant origin using this instruction. --------- Signed-off-by:
Adrian Catangiu <adrian@parity.io> Co-authored-by:
Adrian Catangiu <adrian@parity.io> Co-authored-by:
Andrii <ndk@parity.io> Co-authored-by:
Branislav Kontur <bkontur@gmail.com> Co-authored-by:
Joseph Zhao <65984904+programskillforverification@users.noreply.github.com> Co-authored-by:
Nazar Mokrynskyi <nazar@mokrynskyi.com> Co-authored-by:
Bastian Köcher <git@kchr.de> Co-authored-by:
Shawn Tabrizi <shawntabrizi@gmail.com> Co-authored-by: command-bot <>
-
- Nov 11, 2024
-
-
jpserrat authored
Closes #2082 change send xcm to use `xcm::executor::FeeManager` to determine if the sender should be charged. I had to change the `FeeManager` of the penpal config to ensure the same test behaviour as before. For the other tests, I'm using the `FeeManager` from the `xcm::executor::FeeManager` as this one is used to check if the fee can be waived on the charge fees method. --------- Co-authored-by:
Adrian Catangiu <adrian@parity.io> Co-authored-by:
GitHub Action <action@github.com>
-
- Nov 06, 2024
-
-
Francisco Aguirre authored
# Context This PR aims to introduce XCMv5, for now it's in progress and will be updated over time. This branch will serve as a milestone branch for merging in all features we want to add to XCM, roughly outlined [here](https://github.com/polkadot-fellows/xcm-format/issues/60). More features could be added. ## TODO - [x] Migrate foreign assets from v3 to v4 - [x] Setup v5 skeleton - [x] Remove XCMv2 - [x] https://github.com/paritytech/polkadot-sdk/pull/5390 - [x] https://github.com/paritytech/polkadot-sdk/pull/5585 - [x] https://github.com/paritytech/polkadot-sdk/pull/5420 - [x] https://github.com/paritytech/polkadot-sdk/pull/5876 - [x] https://github.com/paritytech/polkadot-sdk/pull/5971 - [x] https://github.com/paritytech/polkadot-sdk/pull/6148 - [x] https://github.com/paritytech/polkadot-sdk/pull/6228 Fixes #3434 Fixes https://github.com/paritytech/polkadot-sdk/issues/4190 Fixes https://github.com/paritytech/polkadot-sdk/issues/5209 Fixes https://github.com/paritytech/polkadot-sdk/issues/5241 Fixes https://github.com/paritytech/polkadot-sdk/issues/4284 --------- Signed-off-by:
Adrian Catangiu <adrian@parity.io> Co-authored-by:
Adrian Catangiu <adrian@parity.io> Co-authored-by:
Andrii <ndk@parity.io> Co-authored-by:
Branislav Kontur <bkontur@gmail.com> Co-authored-by:
Joseph Zhao <65984904+programskillforverification@users.noreply.github.com> Co-authored-by:
Nazar Mokrynskyi <nazar@mokrynskyi.com> Co-authored-by:
Bastian Köcher <git@kchr.de> Co-authored-by:
Shawn Tabrizi <shawntabrizi@gmail.com> Co-authored-by: command-bot <> Co-authored-by:
GitHub Action <action@github.com> Co-authored-by:
Serban Iorga <serban@parity.io>
-
- Oct 25, 2024
-
-
Branislav Kontur authored
Relates to: https://github.com/paritytech/polkadot-sdk/pull/4826 Relates to: https://github.com/paritytech/polkadot-sdk/issues/3214 ## Description `pallet-xcm` stores some operational data that uses `Versioned*` XCM types. When we add a new XCM version (XV), we deprecate XV-2 and remove XV-3. Without proper migration, this can lead to issues with [undecodable storage](https://github.com/paritytech/polkadot-sdk/actions/runs/11381324568/job/31662577532?pr=6092), as was identified on the XCMv5 branch where XCMv2 was removed. This PR extends the existing `MigrateToLatestXcmVersion` to include migration for the `Queries`, `LockedFungibles`, and `RemoteLockedFungibles` storage types. Additionally, more checks were added to `try_state` for these types. ## TODO - [x] create tracking issue for `polkadot-fellows` https://github.com/polkadot-fellows/runtimes/issues/492 - [x] Add missing `MigrateToLatestXcmVersion` for westend - [x] fix pallet-xcm `Queries` - fails for Westend https://github.com/paritytech/polkadot-sdk/actions/runs/11381324568/job/31662577532?pr=6092 - `V2` was removed from `Versioned*` stuff, but we have a live data with V2 e.g. Queries - e.g. Kusama or Polkadot relay chains ``` VersionNotifier: { origin: { V2: { parents: 0 interior: { X1: { Parachain: 2,124 } } } } isActive: true } ``` 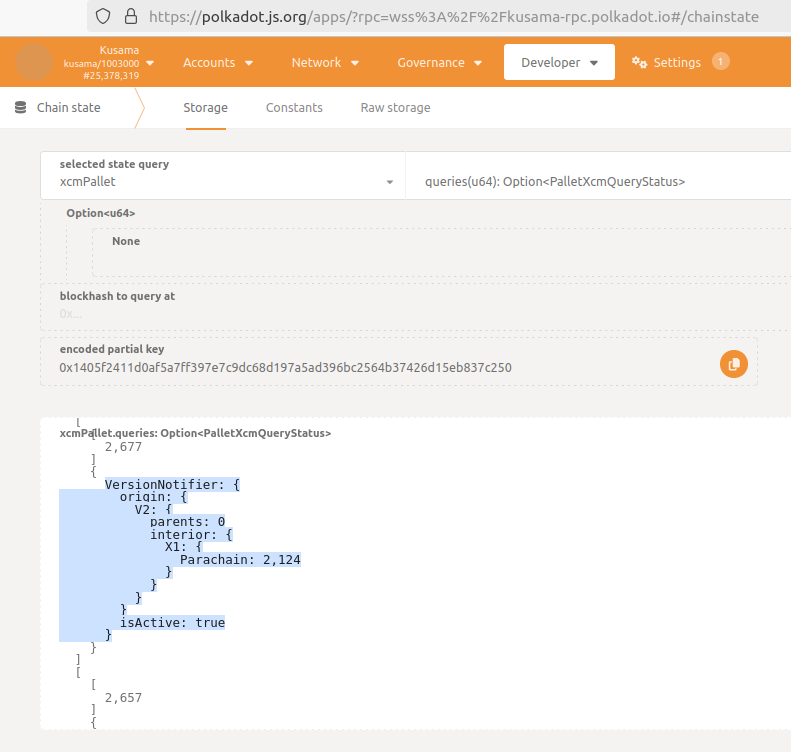 - [x] fix also for `RemoteLockedFungibles` - [x] fix also for `LockedFungibles` ## Follow-ups - [ ] deploy on Westend chains before XCMv5 - [ ] https://github.com/paritytech/polkadot-sdk/issues/6188 --------- Co-authored-by: command-bot <> Co-authored-by:GitHub Action <action@github.com> Co-authored-by:
Francisco Aguirre <franciscoaguirreperez@gmail.com>
-
- Oct 22, 2024
-
-
Serban Iorga authored
Related to https://github.com/paritytech/polkadot-sdk/issues/6161 This seems to fix the `JavaScript heap out of memory` error encountered in the bridge zombienet tests lately. This is just a partial fix, since we also need to address https://github.com/paritytech/polkadot-sdk/issues/6133 in order to fully fix the bridge zombienet tests
-
- Oct 21, 2024
-
-
Andrii authored
Changed returned type of API methods from `Result<bool, xcm_runtime_apis::trusted_query::Error>` to a typed one `type XcmTrustedQueryResult = Result<bool, xcm_runtime_apis::trusted_query::Error>;` Follow-up of [PR-6039](https://github.com/paritytech/polkadot-sdk/pull/6039) --------- Co-authored-by:
Bastian Köcher <git@kchr.de> Co-authored-by:
Adrian Catangiu <adrian@parity.io>
-
- Oct 18, 2024
-
-
georgepisaltu authored
Original PR https://github.com/paritytech/polkadot-sdk/pull/2280 reverted in https://github.com/paritytech/polkadot-sdk/pull/3665 This PR reintroduces the reverted functionality with additional changes, related effort [here](https://github.com/paritytech/polkadot-sdk/pull/3623). Description is copied over from the original PR First part of [Extrinsic Horizon](https://github.com/paritytech/polkadot-sdk/issues/2415) Introduces a new trait `TransactionExtension` to replace `SignedExtension`. Introduce the idea of transactions which obey the runtime's extensions and have according Extension data (né Extra data) yet do not have hard-coded signatures. Deprecate the terminology of "Unsigned" when used for transactions/extrinsics owing to there now being "proper" unsigned transactions which obey the extension framework and "old-style" unsigned which do not. Instead we have __*General*__ for the former and __*Bare*__ for the latter. (Ultimately, the latter will be phased out as a type of transaction, and Bare will only be used for Inherents.) Types of extrinsic are now therefore: - Bare (no hardcoded signature, no Extra data; used to be known as "Unsigned") - Bare transactions (deprecated): Gossiped, validated with `ValidateUnsigned` (deprecated) and the `_bare_compat` bits of `TransactionExtension` (deprecated). - Inherents: Not gossiped, validated with `ProvideInherent`. - Extended (Extra data): Gossiped, validated via `TransactionExtension`. - Signed transactions (with a hardcoded signature) in extrinsic v4. - General transactions (without a hardcoded signature) in extrinsic v5. `TransactionExtension` differs from `SignedExtension` because: - A signature on the underlying transaction may validly not be present. - It may alter the origin during validation. - `pre_dispatch` is renamed to `prepare` and need not contain the checks present in `validate`. - `validate` and `prepare` is passed an `Origin` rather than a `AccountId`. - `validate` may pass arbitrary information into `prepare` via a new user-specifiable type `Val`. - `AdditionalSigned`/`additional_signed` is renamed to `Implicit`/`implicit`. It is encoded *for the entire transaction* and passed in to each extension as a new argument to `validate`. This facilitates the ability of extensions to acts as underlying crypto. There is a new `DispatchTransaction` trait which contains only default function impls and is impl'ed for any `TransactionExtension` impler. It provides several utility functions which reduce some of the tedium from using `TransactionExtension` (indeed, none of its regular functions should now need to be called directly). Three transaction version discriminator ("versions") are now permissible (RFC [here](https://github.com/polkadot-fellows/RFCs/pull/84)) in extrinsic version 5: - 0b00000100 or 0b00000101: Bare (used to be called "Unsigned"): contains Signature or Extra (extension data). After bare transactions are no longer supported, this will strictly identify an Inherents only. Available in both extrinsic versions 4 and 5. - 0b10000100: Old-school "Signed" Transaction: contains Signature, Extra (extension data) and an extension version byte, introduced as part of [RFC99](https://github.com/polkadot-fellows/RFCs/blob/main/text/0099-transaction-extension-version.md). Still available as part of extrinsic v4. - 0b01000101: New-school "General" Transaction: contains Extra (extension data) and an extension version byte, as per RFC99, but no Signature. Only available in extrinsic v5. For the New-school General Transaction, it becomes trivial for authors to publish extensions to the mechanism for authorizing an Origin, e.g. through new kinds of key-signing schemes, ZK proofs, pallet state, mutations over pre-authenticated origins or any combination of the above. `UncheckedExtrinsic` still maintains encode/decode backwards compatibility with extrinsic version 4, where the first byte was encoded as: - 0b00000100 - Unsigned transactions - 0b10000100 - Old-school Signed transactions, without the extension version byte Now, `UncheckedExtrinsic` contains a `Preamble` and the actual call. The `Preamble` describes the type of extrinsic as follows: ```rust /// A "header" for extrinsics leading up to the call itself. Determines the type of extrinsic and /// holds any necessary specialized data. #[derive(Eq, PartialEq, Clone)] pub enum Preamble<Address, Signature, Extension> { /// An extrinsic without a signature or any extension. This means it's either an inherent or /// an old-school "Unsigned" (we don't use that terminology any more since it's confusable with /// the general transaction which is without a signature but does have an extension). /// /// NOTE: In the future, once we remove `ValidateUnsigned`, this will only serve Inherent /// extrinsics and thus can be renamed to `Inherent`. Bare(ExtrinsicVersion), /// An old-school transaction extrinsic which includes a signature of some hard-coded crypto. /// Available only on extrinsic version 4. Signed(Address, Signature, ExtensionVersion, Extension), /// A new-school transaction extrinsic which does not include a signature by default. The /// origin authorization, through signatures or other means, is performed by the transaction /// extension in this extrinsic. Available starting with extrinsic version 5. General(ExtensionVersion, Extension), } ``` ## Code Migration ### NOW: Getting it to build Wrap your `SignedExtension`s in `AsTransactionExtension`. This should be accompanied by renaming your aggregate type in line with the new terminology. E.g. Before: ```rust /// The SignedExtension to the basic transaction logic. pub type SignedExtra = ( /* snip */ MySpecialSignedExtension, ); /// Unchecked extrinsic type as expected by this runtime. pub type UncheckedExtrinsic = generic::UncheckedExtrinsic<Address, RuntimeCall, Signature, SignedExtra>; ``` After: ```rust /// The extension to the basic transaction logic. pub type TxExtension = ( /* snip */ AsTransactionExtension<MySpecialSignedExtension>, ); /// Unchecked extrinsic type as expected by this runtime. pub type UncheckedExtrinsic = generic::UncheckedExtrinsic<Address, RuntimeCall, Signature, TxExtension>; ``` You'll also need to alter any transaction building logic to add a `.into()` to make the conversion happen. E.g. Before: ```rust fn construct_extrinsic( /* snip */ ) -> UncheckedExtrinsic { let extra: SignedExtra = ( /* snip */ MySpecialSignedExtension::new(/* snip */), ); let payload = SignedPayload::new(call.clone(), extra.clone()).unwrap(); let signature = payload.using_encoded(|e| sender.sign(e)); UncheckedExtrinsic::new_signed( /* snip */ Signature::Sr25519(signature), extra, ) } ``` After: ```rust fn construct_extrinsic( /* snip */ ) -> UncheckedExtrinsic { let tx_ext: TxExtension = ( /* snip */ MySpecialSignedExtension::new(/* snip */).into(), ); let payload = SignedPayload::new(call.clone(), tx_ext.clone()).unwrap(); let signature = payload.using_encoded(|e| sender.sign(e)); UncheckedExtrinsic::new_signed( /* snip */ Signature::Sr25519(signature), tx_ext, ) } ``` ### SOON: Migrating to `TransactionExtension` Most `SignedExtension`s can be trivially converted to become a `TransactionExtension`. There are a few things to know. - Instead of a single trait like `SignedExtension`, you should now implement two traits individually: `TransactionExtensionBase` and `TransactionExtension`. - Weights are now a thing and must be provided via the new function `fn weight`. #### `TransactionExtensionBase` This trait takes care of anything which is not dependent on types specific to your runtime, most notably `Call`. - `AdditionalSigned`/`additional_signed` is renamed to `Implicit`/`implicit`. - Weight must be returned by implementing the `weight` function. If your extension is associated with a pallet, you'll probably want to do this via the pallet's existing benchmarking infrastructure. #### `TransactionExtension` Generally: - `pre_dispatch` is now `prepare` and you *should not reexecute the `validate` functionality in there*! - You don't get an account ID any more; you get an origin instead. If you need to presume an account ID, then you can use the trait function `AsSystemOriginSigner::as_system_origin_signer`. - You get an additional ticket, similar to `Pre`, called `Val`. This defines data which is passed from `validate` into `prepare`. This is important since you should not be duplicating logic from `validate` to `prepare`, you need a way of passing your working from the former into the latter. This is it. - This trait takes a `Call` type parameter. `Call` is the runtime call type which used to be an associated type; you can just move it to become a type parameter for your trait impl. - There's no `AccountId` associated type any more. Just remove it. Regarding `validate`: - You get three new parameters in `validate`; all can be ignored when migrating from `SignedExtension`. - `validate` returns a tuple on success; the second item in the tuple is the new ticket type `Self::Val` which gets passed in to `prepare`. If you use any information extracted during `validate` (off-chain and on-chain, non-mutating) in `prepare` (on-chain, mutating) then you can pass it through with this. For the tuple's last item, just return the `origin` argument. Regarding `prepare`: - This is renamed from `pre_dispatch`, but there is one change: - FUNCTIONALITY TO VALIDATE THE TRANSACTION NEED NOT BE DUPLICATED FROM `validate`!! - (This is different to `SignedExtension` which was required to run the same checks in `pre_dispatch` as in `validate`.) Regarding `post_dispatch`: - Since there are no unsigned transactions handled by `TransactionExtension`, `Pre` is always defined, so the first parameter is `Self::Pre` rather than `Option<Self::Pre>`. If you make use of `SignedExtension::validate_unsigned` or `SignedExtension::pre_dispatch_unsigned`, then: - Just use the regular versions of these functions instead. - Have your logic execute in the case that the `origin` is `None`. - Ensure your transaction creation logic creates a General Transaction rather than a Bare Transaction; this means having to include all `TransactionExtension`s' data. - `ValidateUnsigned` can still be used (for now) if you need to be able to construct transactions which contain none of the extension data, however these will be phased out in stage 2 of the Transactions Horizon, so you should consider moving to an extension-centric design. --------- Signed-off-by:georgepisaltu <george.pisaltu@parity.io> Co-authored-by:
Guillaume Thiolliere <gui.thiolliere@gmail.com> Co-authored-by:
Branislav Kontur <bkontur@gmail.com>
-
- Oct 17, 2024
-
-
Andrii authored
Implemented is_trusted_reserve and is_trusted_teleporter API methods. Tested them with regular and chopstick tests. Fixes #97 --------- Co-authored-by:Francisco Aguirre <franciscoaguirreperez@gmail.com>
-
Joseph Zhao authored
Closes #5705 --------- Co-authored-by:
Iulian Barbu <14218860+iulianbarbu@users.noreply.github.com> Co-authored-by:
Michal Kucharczyk <1728078+michalkucharczyk@users.noreply.github.com>
-
- Oct 15, 2024
-
-
Ayevbeosa Iyamu authored
Added error logs in pallet-xcm to help in debugging, fixes #2408 ## TODO - [x] change `log::error` to `tracing::error` format for `xcm-executor` - [x] check existing logs, e.g. this one can be extended with more info `tracing::error!(target: "xcm::reanchor", ?error, "Failed reanchoring with error");` - [x] use `tracing` instead of `log` for `pallet-xcm/src/lib.rs` --------- Co-authored-by:
Ayevbeosa Iyamu <aiyamu@vatebra.com> Co-authored-by:
Adrian Catangiu <adrian@parity.io> Co-authored-by:
Francisco Aguirre <franciscoaguirreperez@gmail.com> Co-authored-by:
Branislav Kontur <bkontur@gmail.com> Co-authored-by:
Bastian Köcher <git@kchr.de>
-
- Oct 10, 2024
-
-
Francisco Aguirre authored
# Description This PR addresses https://github.com/paritytech/polkadot-sdk/issues/5878. After dry running an xcm on asset hub, we had redundant xcms showing up in the `forwarded_xcms` field of the dry run effects returned. These were caused by two things: - The `UpwardMessageSender` router always added an element even if there were no messages. - The two routers on asset hub westend related to bridging (to rococo and sepolia) getting the message from their queues when their queues is actually the same xcmp queue that was already contemplated. In order to fix this, we check for no messages in UMP and clear the implementation of `InspectMessageQueues` for these bridging routers. Keep in mind that the bridged message is still sent, as normal via the xcmp-queue to Bridge Hub. To keep on dry-running the journey of the message, the next hop to dry-run is Bridge Hub. That'll be tackled in a different PR. Added a test in `bridge-hub-westend-integration-tests` and `bridge-hub-rococo-integration-tests` that show that dry-running a transfer across the bridge from asset hub results in one and only one message sent to bridge hub. ## TODO - [x] Functionality - [x] Test --------- Co-authored-by: command-bot <>
-
- Oct 07, 2024
-
-
Juan Ignacio Rios authored
# Description ## What? Make it possible for other pallets to implement their own logic when a slash on a balance occurs. ## Why? In the [introduction of holds](https://github.com/paritytech/substrate/pull/12951) @gavofyork said: > Since Holds are designed to be infallibly slashed, this means that any logic using a Freeze must handle the possibility of the frozen amount being reduced, potentially to zero. A permissionless function should be provided in order to allow bookkeeping to be updated in this instance. At Polimec we needed to find a way to reduce the vesting schedules of our users after a slash was made, and after talking to @Kianenigma at the Web3Summit, we realized there was no easy way to implement this with the current traits, so we came up with this solution. ## How? - First we abstract the `done_slash` function of holds::Balanced to it's own trait that any pallet can implement. - Then we add a config type in pallet-balances that accepts a callback tuple of all the pallets that implement this trait. - Finally implement done_slash for pallet-balances such that it calls the config type. ## Integration The default implementation of done_slash is still an empty function, and the new config type of pallet-balances can be set to an empty tuple, so nothing changes by default. ## Review Notes - I suggest to focus on the first commit which contains the main logic changes. - I also have a working implementation of done_slash for pallet_vesting, should I add it to this PR? - If I run `cargo +nightly fmt --all` then I get changes to a lot of unrelated crates, so not sure if I should run it to avoid the fmt failure of the CI - Should I hunt down references to fungible/fungibles documentation and update it accordingly? **Polkadot address:** `15fj1UhQp8Xes7y7LSmDYTy349mXvUwrbNmLaP5tQKBxsQY1` # Checklist * [x] My PR includes a detailed description as outlined in the "Description" and its two subsections above. * [x] My PR follows the [labeling requirements]( https://github.com/paritytech/polkadot-sdk/blob/master/docs/contributor/CONTRIBUTING.md#Process ) of this project (at minimum one label for `T` required) * External contributors: ask maintainers to put the right label on your PR. * [ ] I have made corresponding changes to the documentation (if applicable) --------- Co-authored-by:
Kian Paimani <5588131+kianenigma@users.noreply.github.com> Co-authored-by: command-bot <> Co-authored-by:
Francisco Aguirre <franciscoaguirreperez@gmail.com>
-
- Oct 05, 2024
-
-
Adrian Catangiu authored
The AllowTopLevelPaidExecutionFrom allows ClearOrigin instructions before the expected BuyExecution instruction, it also allows messages without any origin altering instructions. This commit enhances the barrier to also support messages that use AliasOrigin, or DescendOrigin. This is sometimes desired in asset transfer XCM programs that need to run the inbound assets instructions using the origin chain root origin, but then want to drop privileges for the rest of the program. Currently these programs drop privileges by clearing the origin completely, but that also unnecessarily limits the range of actions available to the rest of the program. Using DescendOrigin or AliasOrigin allows the sending chain to instruct the receiving chain what the deprivileged real origin is. See https://github.com/polkadot-fellows/RFCs/pull/109 and https://github.com/polkadot-fellows/RFCs/pull/122 for more details on how DescendOrigin and AliasOrigin could be used instead of ClearOrigin. --------- Signed-off-by:Adrian Catangiu <adrian@parity.io>
-
- Sep 26, 2024
-
-
Alexander Samusev authored
cc https://github.com/paritytech/ci_cd/issues/1035 cc https://github.com/paritytech/ci_cd/issues/1023 --------- Signed-off-by:
Oliver Tale-Yazdi <oliver.tale-yazdi@parity.io> Co-authored-by: command-bot <> Co-authored-by:
Maksym H <1177472+mordamax@users.noreply.github.com> Co-authored-by:
gui <gui.thiolliere@gmail.com> Co-authored-by:
Oliver Tale-Yazdi <oliver.tale-yazdi@parity.io> Co-authored-by:
Bastian Köcher <git@kchr.de> Co-authored-by:
ggwpez <ggwpez@users.noreply.github.com>
-
- Sep 25, 2024
-
-
Adrian Catangiu authored
This change adds the required validation for stronger UX guarantees when using `InitiateReserveWithdraw` or `InitiateTeleport` XCM instructions. Execution of the instructions will fail if the local chain is not configured to trust the "destination" or "reserve" chain as a reserve/trusted-teleporter for the provided "assets". With this change, misuse of `InitiateReserveWithdraw`/`InitiateTeleport` fails on origin with no overall side-effects, rather than failing on destination (with side-effects to origin's assets issuance). The commit also makes the same validations for pallet-xcm transfers, and adds regression tests. --------- Signed-off-by:
Adrian Catangiu <adrian@parity.io> Co-authored-by:
Branislav Kontur <bkontur@gmail.com>
-