- Jan 27, 2025
-
-
dharjeezy authored
-
- Jan 25, 2025
-
-
dharjeezy authored
-
- Jan 24, 2025
-
-
Andrei Eres authored
The link to Polkachu is not working
-
Alexander Theißen authored
This regression was introduced with some of the recent PRs. Regression fixed and test added. --------- Co-authored-by:cmd[bot] <41898282+github-actions[bot]@users.noreply.github.com>
-
PG Herveou authored
- Add option to specify database_url using DATABASE_URL environment variable - Add a eth-rpc-tester rust bin that can be used to test deployment before releasing eth-rpc - make evm_block non fallible so that it can return an Ok response for older blocks when the runtime API is not available - update cargo.lock to integrate changes from https://github.com/paritytech/subxt/pull/1904 --------- Co-authored-by:cmd[bot] <41898282+github-actions[bot]@users.noreply.github.com>
-
Maksym H authored
Closes #6196 Closes #7204 Example of PR: https://github.com/paritytech/polkadot-sdk/pull/6816 Every sunday 01:00 AM it's going to start to benchmark (with /cmd bench) all runtimes and all pallets Then diff total will be pushed to a branch and PR open,. I assume review-bot is going assign required reviewers per changed files I afraid each weeks will be too much to review & merge, but we can adjust later Bonus: fix for pallet_multisig lib and substrate/.maintain/frame-weight-template.hbs , which didn't let to compile new weights --------- Signed-off-by:
Oliver Tale-Yazdi <oliver.tale-yazdi@parity.io> Co-authored-by: command-bot <> Co-authored-by:
cmd[bot] <41898282+github-actions[bot]@users.noreply.github.com> Co-authored-by:
Oliver Tale-Yazdi <oliver.tale-yazdi@parity.io>
-
- Jan 23, 2025
-
-
Alisher A. Khassanov authored
# Description Closes https://github.com/paritytech/polkadot-sdk/issues/7265. ## Integration Requires changes in `https://github.com/polkadot-js/api/packages/{rpc-augment,types-support,types}` to be visible in Polkadot\Substrate Portal and in other libraries where we should explicitly state RPC methods. Accompany PR to `polkadot-js/api`: https://github.com/polkadot-js/api/pull/6070. ## Review Notes Please put the right label on my PR. --------- Co-authored-by: command-bot <> Co-authored-by:Bastian Köcher <git@kchr.de>
-
runcomet authored
# Derived Dev Accounts Resolves https://github.com/paritytech/polkadot-sdk/issues/6040 ## Description This update introduces support for creating an arbitrary number of developer accounts at the genesis block based on a specified derivation path. This functionality is gated by the runtime-benchmarks feature, ensuring it is only enabled during benchmarking scenarios. ### Key Features - Arbitrary Dev Accounts at Genesis: Developers can now specify any number of accounts to be generated at genesis using a hard derivation path. - Default Derivation Path: If no derivation path is provided (i.e., when `Option<dev_accounts: (..., None)>` is set to `Some` at genesis), the system will default to the path `//Sender//{}`. - No Impact on Total Token Issuance: Developer accounts are excluded from the total issuance of the token supply at genesis, ensuring they do not affect the overall balance or token distribution. polkadot address: 14SRqZTC1d8rfxL8W1tBTnfUBPU23ACFVPzp61FyGf4ftUFg --------- Co-authored-by:Sebastian Kunert <skunert49@gmail.com>
-
PG Herveou authored
- Fix the EVM fee cost estimation. The estimation shown in EVM wallet was using Native instead of EVM decimals - Remove the precise code length estimation in dry run call. Over-estimating is fine, since extra gas is refunded anyway. - Ensure that the estimated fee calculated from gas_price x gas use the encoded weight & deposit limit instead of the exact one calculated by the dry-run. Else we can end up with a fee that is lower than the actual fee paid by the user --------- Co-authored-by: command-bot <>
-
- Jan 22, 2025
-
-
FereMouSiopi authored
Part of https://github.com/paritytech/polkadot-sdk/issues/6504 --------- Co-authored-by: command-bot <> Co-authored-by:Bastian Köcher <git@kchr.de>
-
Alexandru Vasile authored
This PR enforces that outbound requests are finished within the specified protocol timeout. The stable2412 version running libp2p 0.52.4 contains a bug which does not track request timeouts properly: - https://github.com/libp2p/rust-libp2p/pull/5429 The issue has been detected while submitting libp2p -> litep2p requests in kusama. This aims to check that pending outbound requests have not timedout. Although the issue has been fixed in libp2p, there might be other cases where this may happen. For example: - https://github.com/libp2p/rust-libp2p/pull/5417 For more context see: https://github.com/paritytech/polkadot-sdk/issues/7076#issuecomment-2596085096 1. Ideally, the force-timeout mechanism in this PR should never be triggered in production. However, origin/stable2412 occasionally encounters this issue. When this happens, 2 warnings may be generated: - one warning introduced by this PR wrt force timeout terminating the request - possible one warning when the libp2p decides (if at all) to provide the response back to substrate (as mentioned by @alexggh [here](https://github.com/paritytech/polkadot-sdk/pull/7222/files#diff-052aeaf79fef3d9a18c2cfd67006aa306b8d52e848509d9077a6a0f2eb856af7L769) and [here](https://github.com/paritytech/polkadot-sdk/pull/7222/files#diff-052aeaf79fef3d9a18c2cfd67006aa306b8d52e848509d9077a6a0f2eb856af7L842) 2. This implementation does not propagate to the substrate service the `RequestFinished { error: .. }`. That event is only used internally by substrate to increment metrics. However, we don't have the peer information available to propagate the event properly when we force-timeout the request. Considering this should most likely not happen in production (origin/master) and that we'll be able to extract information by warnings, I would say this is a good tradeoff for code simplicity: https://github.com/paritytech/polkadot-sdk/blob/06e3b5c6 /substrate/client/network/src/service.rs#L1543 ### Testing Added a new test to ensure the timeout is reached properly, even if libp2p does not produce a response in due time. I've also transitioned the tests to using `tokio::test` due to a limitation of [CI](https://github.com/paritytech/polkadot-sdk/actions/runs/12832055737/job/35784043867) ``` --- TRY 1 STDERR: sc-network request_responses::tests::max_response_size_exceeded --- thread 'request_responses::tests::max_response_size_exceeded' panicked at /usr/local/cargo/registry/src/index.crates.io-6f17d22bba15001f/tokio-1.40.0/src/time/interval.rs:139:26: there is no reactor running, must be called from the context of a Tokio 1.x runtime ``` cc @paritytech/networking --------- Signed-off-by:
Alexandru Vasile <alexandru.vasile@parity.io> Co-authored-by:
Bastian Köcher <git@kchr.de>
-
Serban Iorga authored
Related to https://github.com/paritytech/polkadot-sdk/issues/4523 Follow-up for: https://github.com/paritytech/polkadot-sdk/pull/5188 Reopening https://github.com/paritytech/polkadot-sdk/pull/6732 as a new PR --------- Co-authored-by: command-bot <>
-
- Jan 21, 2025
-
-
Ludovic_Domingues authored
Part of #6504 --------- Co-authored-by:
Bastian Köcher <git@kchr.de> Co-authored-by:
Giuseppe Re <giuseppe.re@parity.io>
-
Sebastian Kunert authored
Link-checker job is constantly failing because of these two links. In the browser there is a redirect, apparently our lychee checker can't handle it.
-
- Jan 20, 2025
-
-
PG Herveou authored
For eth-indexer, it's probably safer to use `subscribe_finalized` and index these blocks into the DB rather than `subscribe_best` --------- Co-authored-by: command-bot <>
-
Benjamin Gallois authored
## Description The `frame-benchmarking-cli` crate has not been buildable without the `rocksdb` feature since version 1.17.0. **Error:** ```rust self.database()?.unwrap_or(Database::RocksDb), ^^^^^^^ variant or associated item not found in `Database` ``` This issue is also related to the `rocksdb` feature bleeding (#3793), where the `rocksdb` feature was always activated even when compiling this crate with `--no-default-features`. **Fix:** - Resolved the error by choosing `paritydb` as the default database when compiled without the `rocksdb` feature. - Fixed the issue where the `sc-cli` crate's `rocksdb` feature was always active, even compiling `frame-benchmarking-cli` with `--no-default-features`. ## Review Notes Fix the crate to be built without rocksdb, not intended to solve #3793. --------- Co-authored-by: command-bot <> -
runcomet authored
Part of https://github.com/paritytech/polkadot-sdk/issues/6504 ### Added modules - `utility`: Traits not tied to any direct operation in the runtime. polkadot address: 14SRqZTC1d8rfxL8W1tBTnfUBPU23ACFVPzp61FyGf4ftUFg --------- Co-authored-by:Giuseppe Re <giuseppe.re@parity.io>
-
Ron authored
Part of https://github.com/paritytech/polkadot-sdk/issues/6504
-
PG Herveou authored
Log error instead of failing with an error when block processing fails --------- Co-authored-by: command-bot <>
-
- Jan 17, 2025
-
-
PG Herveou authored
Add foundation for supporting call traces in pallet_revive Follow up: - PR #7167 Add changes to eth-rpc to introduce debug endpoint that will use pallet-revive tracing features - PR #6727 Add new RPC to the client and implement tracing runtime API that can capture traces on previous blocks --------- Co-authored-by:Alexander Theißen <alex.theissen@me.com>
-
Alexander Theißen authored
Update to PolkaVM `0.19`. This version renumbers the opcodes in order to be in-line with the grey paper. Hopefully, for the last time. This means that it breaks existing contracts. --------- Signed-off-by:
xermicus <cyrill@parity.io> Co-authored-by: command-bot <> Co-authored-by:
xermicus <cyrill@parity.io>
-
thiolliere authored
We already use it for lots of pallet. Keeping it feature gated by experimental means we lose the information of which pallet was using experimental before the migration to frame crate usage. We can consider `polkadot-sdk-frame` crate unstable but let's not use the feature `experimental`. --------- Co-authored-by: command-bot <>
-
- Jan 16, 2025
-
-
Ankan authored
Migrate staking currency from `traits::LockableCurrency` to `traits::fungible::holds`. Resolves part of https://github.com/paritytech/polkadot-sdk/issues/226. ## Changes ### Nomination Pool TransferStake is now incompatible with fungible migration as old pools were not meant to have additional ED. Since they are anyways deprecated, removed its usage from all test runtimes. ### Staking - Config: `Currency` becomes of type `Fungible` while `OldCurrency` is the `LockableCurrency` used before. - Lazy migration of accounts. Any ledger update will create a new hold with no extra reads/writes. A permissionless extrinsic `migrate_currency()` releases the old `lock` along with some housekeeping. - Staking now requires ED to be left free. It also adds no consumer to staking accounts. - If hold cannot be applied to all stake, the un-holdable part is force withdrawn from the ledger. ### Delegated Staking The pallet does not add provider for agents anymore. ## Migration stats ### Polkadot Total accounts that can be migrated: 59564 Accounts failing to migrate: 0 Accounts with stake force withdrawn greater than ED: 59 Total force withdrawal: 29591.26 DOT ### Kusama Total accounts that can be migrated: 26311 Accounts failing to migrate: 0 Accounts with stake force withdrawn greater than ED: 48 Total force withdrawal: 1036.05 KSM [Full logs here](https://hackmd.io/@ak0n/BklDuFra0). ## Note about locks (freeze) vs holds With locks or freezes, staking could use total balance of an account. But with holds, the account needs to be left with at least Existential Deposit in free balance. This would also affect nomination pools which till now has been able to stake all funds contributed to it. An alternate version of this PR is https://github.com/paritytech/polkadot-sdk/pull/5658 where staking pallet does not add any provider, but means pools and delegated-staking pallet has to provide for these accounts and makes the end to end logic (of provider and consumer ref) lot less intuitive and prone to bug. This PR now introduces requirement for stakers to maintain ED in their free balance. This helps with removing the bug prone incrementing and decrementing of consumers and providers. ## TODO - [x] Test: Vesting + governance locked funds can be staked. - [ ] can `Call::restore_ledger` be removed? @gpestana - [x] Ensure unclaimed withdrawals is not affected by no provider for pool accounts. - [x] Investigate kusama accounts with balance between 0 and ED. - [x] Permissionless call to release lock. - [x] Migration of consumer (dec) and provider (inc) for direct stakers. - [x] force unstake if hold cannot be applied to all stake. - [x] Fix try state checks (it thinks nothing is staked for unmigrated ledgers). - [x] Bench `migrate_currency`. - [x] Virtual Staker migration test. - [x] Ensure total issuance is upto date when minting rewards. ## Followup - https://github.com/paritytech/polkadot-sdk/issues/5742 --------- Co-authored-by: command-bot <>
-
Dastan authored
closes https://github.com/paritytech/polkadot-sdk/issues/6911
-
Liam Aharon authored
Closes #3149 ## Description This PR introduces `pallet-asset-rewards`, which allows accounts to be rewarded for freezing `fungible` tokens. The motivation for creating this pallet is to allow incentivising LPs. See the pallet docs for more info about the pallet. ## Runtime changes The pallet has been added to - `asset-hub-rococo` - `asset-hub-westend` The `NativeAndAssets` `fungibles` Union did not contain `PoolAssets`, so it has been renamed `NativeAndNonPoolAssets` A new `fungibles` Union `NativeAndAllAssets` was created to encompass all assets and the native token. ## TODO - [x] Emulation tests - [x] Fill in Freeze logic (blocked https://github.com/paritytech/polkadot-sdk/issues/3342) and re-run benchmarks --------- Co-authored-by: command-bot <> Co-authored-by:
Oliver Tale-Yazdi <oliver.tale-yazdi@parity.io> Co-authored-by:
muharem <ismailov.m.h@gmail.com> Co-authored-by:
Guillaume Thiolliere <gui.thiolliere@gmail.com>
-
- Jan 15, 2025
-
-
Michael Müller authored
Closes https://github.com/paritytech/polkadot-sdk/issues/6891. cc @athei @xermicus @pgherveou
-
PG Herveou authored
Remove all pallet::events except for the `ContractEmitted` event that is emitted by contracts --------- Co-authored-by: command-bot <> Co-authored-by:Alexander Theißen <alex.theissen@me.com>
-
PG Herveou authored
Remove the `debug_buffer` feature --------- Co-authored-by: command-bot <> Co-authored-by:
Cyrill Leutwiler <cyrill@parity.io> Co-authored-by:
Alexander Theißen <alex.theissen@me.com>
-
Alexandru Vasile authored
This PR provides the partial results of the `GetRecord` kademlia query. This significantly improves the authority discovery records, from ~37 minutes to ~2/3 minutes. In contrast, libp2p discovers authority records in around ~10 minutes. The authority discovery was slow because litep2p provided the records only after the Kademlia query was completed. A normal Kademlia query completes in around 40 seconds to a few minutes. In this PR, partial records are provided as soon as they are discovered from the network. ### Testing Done Started a node in Kusama with `--validator` and litep2p backend. The node discovered 996/1000 authority records in ~ 1 minute 45 seconds. 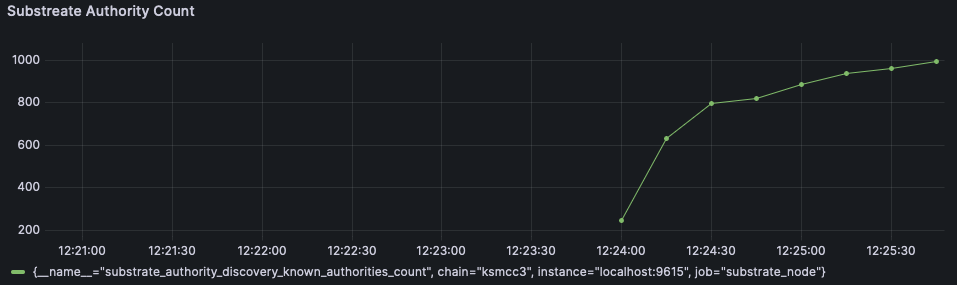 ### Before & After In this image, on the left side is libp2p, in the middle litep2p without this PR, on the right litep2p with this PR 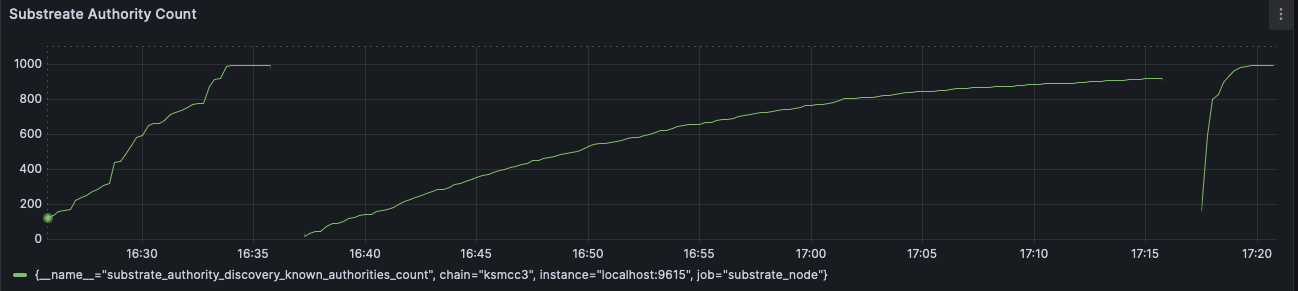 Closes: https://github.com/paritytech/polkadot-sdk/issues/7077 cc @paritytech/networking --------- Signed-off-by:Alexandru Vasile <alexandru.vasile@parity.io>
-
PG Herveou authored
Bump asset-hub westend spec version --------- Co-authored-by: command-bot <>
-
Alexandre R. Baldé authored
Closes #6846 . --------- Signed-off-by:
xermicus <cyrill@parity.io> Co-authored-by: command-bot <> Co-authored-by:
Alexander Theißen <alex.theissen@me.com> Co-authored-by:
xermicus <cyrill@parity.io>
-
Michael Müller authored
Closes https://github.com/paritytech/polkadot-sdk/issues/6767. The return type of the host function `caller_is_root` was denoted as `u32` in `pallet_revive_uapi`. This PR fixes the return type to `bool`. As a drive-by, the PR re-exports `pallet_revive::exec::Origin` to extend what can be tested externally. --------- Co-authored-by:Cyrill Leutwiler <bigcyrill@hotmail.com>
-
Alexandru Vasile authored
This PR rejects inbound requests from banned peers (reputation is below the banned threshold). This mirrors the request-response implementation from the libp2p side. I won't expect this to get triggered too often, but we'll monitor this metric. While at it, have registered a new inbound failure metric to have visibility into this. Discovered during the investigation of: https://github.com/paritytech/polkadot-sdk/issues/7076#issuecomment-2589613046 cc @paritytech/networking --------- Signed-off-by:Alexandru Vasile <alexandru.vasile@parity.io>
-
Xavier Lau authored
Introduce `frame_system::Pallet::run_to_block`, `frame_system::Pallet::run_to_block_with`, and `frame_system::RunToBlockHooks` to establish a generic `run_to_block` mechanism for mock tests, minimizing redundant implementations across various pallets. Closes #299. --- Polkadot address: 156HGo9setPcU2qhFMVWLkcmtCEGySLwNqa3DaEiYSWtte4Y --------- Signed-off-by:
Xavier Lau <x@acg.box> Co-authored-by:
Bastian Köcher <git@kchr.de> Co-authored-by: command-bot <> Co-authored-by:
Guillaume Thiolliere <guillaume.thiolliere@parity.io> Co-authored-by:
Guillaume Thiolliere <gui.thiolliere@gmail.com>
-
Sebastian Kunert authored
Fix error message in `DispatchInfo` where post-dispatch and pre-dispatch weight was reversed. --------- Co-authored-by: command-bot <> Co-authored-by:Bastian Köcher <git@kchr.de>
-
- Jan 14, 2025
-
-
PG Herveou authored
Add an option to persist EVM transaction hash to a SQL db. This should make it possible to run a full archive ETH RPC node (assuming the substrate node is also a full archive node) Some queries such as eth_getTransactionByHash, eth_getBlockTransactionCountByHash, and other need to work with a transaction hash indexes, which are not stored in Substrate and need to be stored by the eth-rpc proxy. The refactoring break down the Client into a `BlockInfoProvider` and `ReceiptProvider` - BlockInfoProvider does not need any persistence data, as we can fetch all block info from the source substrate chain - ReceiptProvider comes in two flavor, - An in memory cache implementation - This is the one we had so far. - A DB implementation - This one persist rows with the block_hash, the transaction_index and the transaction_hash, so that we can later fetch the block and extrinsic for that receipt and reconstruct the ReceiptInfo object. This PR also adds a new binary eth-indexer, that iterate past and new blocks and write the receipt hashes to the DB using the new ReceiptProvider. --------- Co-authored-by:GitHub Action <action@github.com> Co-authored-by: command-bot <>
-
Alexandru Vasile authored
This PR adds the `(litep2p)` suffix to the agent version (user agent) of the identify protocol. The change is needed to gain visibility into network backends and determine exactly the number of validators that are running litep2p. Using tools like subp2p-explorer, we can determine if the validators are running litep2p nodes. This reflects on the identify protocol: ``` info=Identify { protocol_version: Some("/substrate/1.0"), agent_version: Some("polkadot-parachain/v1.17.0-967989c5 (kusama-node-name-01) (litep2p)") ... } ``` cc @paritytech/networking --------- Signed-off-by:Alexandru Vasile <alexandru.vasile@parity.io>
-
Michal Kucharczyk authored
Higher-priority transactions can now replace lower-priority transactions even when the internal _tx_mem_pool_ is full. **Notes for reviewers:** - The _tx_mem_pool_ now maintains information about transaction priority. Although _tx_mem_pool_ itself is stateless, transaction priority is updated after submission to the view. An alternative approach could involve validating transactions at the `at` block, but this is computationally expensive. To avoid additional validation overhead, I opted to use the priority obtained from runtime during submission to the view. This is the rationale behind introducing the `SubmitOutcome` struct, which synchronously communicates transaction priority from the view to the pool. This results in a very brief window during which the transaction priority remains unknown - those transaction are not taken into consideration while dropping takes place. In the future, if needed, we could update transaction priority using view revalidation results to keep this information fully up-to-date (as priority of transaction may change with chain-state evolution). - When _tx_mem_pool_ becomes full (an event anticipated to be rare), transaction priority must be known to perform priority-based removal. In such cases, the most recent block known is utilized for validation. I think that speculative submission to the view and re-using the priority from this submission would be an unnecessary complication. - Once the priority is determined, lower-priority transactions whose cumulative size meets or exceeds the size of the new transaction are collected to ensure the pool size limit is not exceeded. - Transaction removed from _tx_mem_pool_ , also needs to be removed from all the views with appropriate event (which is done by `remove_transaction_subtree`). To ensure complete removal, the `PendingTxReplacement` struct was re-factored to more generic `PendingPreInsertTask` (introduced in #6405) which covers removal and submssion of transaction in the view which may be potentially created in the background. This is to ensure that removed transaction will not re-enter to the newly created view. - `submit_local` implementation was also improved to properly handle priorities in case when mempool is full. Some missing tests for this method were also added. Closes: #5809 --------- Co-authored-by: command-bot <> Co-authored-by:Iulian Barbu <14218860+iulianbarbu@users.noreply.github.com>
-
- Jan 13, 2025
-
-
polka.dom authored
As per #3326, removes pallet::getter macro usage from pallet-grandpa. The syntax `StorageItem::<T, I>::get()` should be used instead. cc @muraca --------- Co-authored-by:Bastian Köcher <git@kchr.de>
-
Michal Kucharczyk authored
# Description This PR modifies the hard-coded size of extrinsics cache within [`PoolRotator`](https://github.com/paritytech/polkadot-sdk/blob/cdf107de/substrate/client/transaction-pool/src/graph/rotator.rs#L36-L45) to be inline with pool limits. The problem was, that due to small size (comparing to number of txs in single block) of hard coded size: https://github.com/paritytech/polkadot-sdk/blob/cdf107de/substrate/client/transaction-pool/src/graph/rotator.rs#L34 excessive number of unnecessary verification were performed in `prune_tags`: https://github.com/paritytech/polkadot-sdk/blob/cdf107de /substrate/client/transaction-pool/src/graph/pool.rs#L369-L370 This was resulting in quite long durations of `prune_tags` execution time (which was ok for 6s, but becomes noticable for 2s blocks): ``` Pruning at HashAndNumber { number: 83, ... }. Resubmitting transactions: 6142, reverification took: 237.818955ms Pruning at HashAndNumber { number: 84, ... }. Resubmitting transactions: 5985, reverification took: 222.118218ms Pruning at HashAndNumber { number: 85, ... }. Resubmitting transactions: 5981, reverification took: 215.546847ms ``` The fix reduces the overhead: ``` Pruning at HashAndNumber { number: 92, ... }. Resubmitting transactions: 6325, reverification took: 14.728354ms Pruning at HashAndNumber { number: 93, ... }. Resubmitting transactions: 7030, reverification took: 23.973607ms Pruning at HashAndNumber { number: 94, ... }. Resubmitting transactions: 4465, reverification took: 9.532472ms ``` ## Review Notes I decided to leave the hardocded `EXPECTED_SIZE` for the legacy transaction pool. Removing verification of transactions during re-submission may negatively impact the behavior of the legacy (single-state) pool. As in long-term we probably want to deprecate old pool, I did not invest time to assess the impact of rotator change in behavior of the legacy pool. --------- Co-authored-by: command-bot <> Co-authored-by:
Iulian Barbu <14218860+iulianbarbu@users.noreply.github.com>
-